Content
- B The Food Delivery Platforms Providing A Logistics Delivery System Like Swiggy And Uber Eats
- Event Mobile Apps
- Steps To Build A Successful Remote Software Development Team
- The Restaurant Side
- Checkout Field Editor For Your Website And Mobile App
- Step 5 Select The Technology Stack Of Food Delivery App Development
- On Demand Food Delivery App Development Package
The app script should also permit you to add one or more features that are essential for you to cater to all the user demands. On-demand delivery is a process of delivering goods and services to the customers whenever and wherever they want them.
They can be filtered by price, cuisine, food category (drinks, meals, main courses, desserts, etc.), cooking time, and ingredients. For example, if a customer has some allergies, they should be able to exclude all dishes with these ingredients with one click.
B The Food Delivery Platforms Providing A Logistics Delivery System Like Swiggy And Uber Eats
Customers can download the mobile app for online ordering from the App Store or Google Play with your brand logo. Jungleworks is a no-code hyperlocal commerce and delivery stack to set up and manage on-demand businesses. The success of really any business depends on its customers and repeat business reinforces how good your business model is. Those companies that are just starting out usually opt to charge the restaurants a fee in exchange for marketing their restaurant. Yes, you can go and edit your food ordering app from the dashboard after you have created it.
Pittsburgh, here are your nominees for the 2021 Technical.ly Awards – technical.ly
Pittsburgh, here are your nominees for the 2021 Technical.ly Awards.
Posted: Wed, 01 Dec 2021 20:39:00 GMT [source]
Now we’ll talk about how to create a food ordering app and make it successful. We’ll talk about both new delivery and full-service on-demand delivery apps.
Filter restaurants and cuisines by ratings, browse through descriptive menus and get what you’re looking for. Enjoy exclusive in-app offers from your favorite restaurants. To check for their design experience,check out food app portfolio on Dribbble. Let’s explore which platforms to create a food ordering app. When we started 2 years ago, the main struggle was to find the right developing team, because the problem was we were all quite demanding in terms of quality. And, this showed that we were able to develop some successful apps. With an estimated value of £30 Billion, Bevy is an on-demand alcohol and snacks delivery app through which users can get a guaranteed 30-minute delivery for their favourite drinks and snacks.
Event Mobile Apps
The restaurant owners need to use push notifications smartly and in a sophisticated manner. Let the customer decide when they want you to send the notifications. You can let customers make payments and book tables well in advance. This will let your customers avoid queues and long waiting hours.
With the multi-language and multi-country support, you can rely on generating the best experiences across every city and country you serve. The entire app launching process involves many steps and paradigms that the publisher has to fulfill to generate excellent results.
Steps To Build A Successful Remote Software Development Team
However, most of the clients that are new to this location will order Starbucks. This is essential to keep in mind when thinking about how to build a delivery app that will succeed. It seems that with this buzz of choices, many apps have fallen into oblivion. In Poland, the number of users of the local delivery service, Pyszne.pl, grew by 50%, which surpasses Uber Eats. In general, as of June 2020, on-demand delivery services are growing worldwide.
- Meaning that once your software registers a limit in time slot bookings or couriers per one area, it automatically takes appropriate actions.
- A detailed list of restaurant information, cuisines list, prices, special combos, prices, and reviews.
- You’ll get paid instantly via your Blackbell app every time a business you referred is charged for their monthly or yearly subscription.
The food delivery market is booming and mobile technologies are shaping it in new ways, making ordering fast for customers and delivering the best service easy for businesses. In this article you’ll find out how to build a mobile food ordering app. Finding a better way in home care site can save a lot of time and energy. We’ll tell you all about the development process and the cost. During your food delivery app development, consider which model is better suited to you and design your software and marketing accordingly, using the help of agencies such as The Marketing Heaven. This gives you clarity of the process of how to create your own delivery app instantly. It significantly helps with tracking the dynamic development of your business to spot weak points and understand what are your strong sides.
The Restaurant Side
Make sure that you provide your users with multiple payment options. Allow your app users to search different restaurants, cafes, pubs, and bars by location and cuisines. Using the search feature, your users can explore different restaurants, dishes, and favorite cuisines. What can a cleaner do in 2 hours is a question you should ask yourself before hiring an cleaning agency. Get the best deals on kitchen remodeling services in fort collins at www.fortcollinshandyman.net/ website. These are all the features you’ll need to build three standalone apps that will sync data and make the delivery process easy and smooth. Now let’s find out how much it will cost to make all these apps. The UpMenu online ordering system also supports remote orders in restaurant chains.
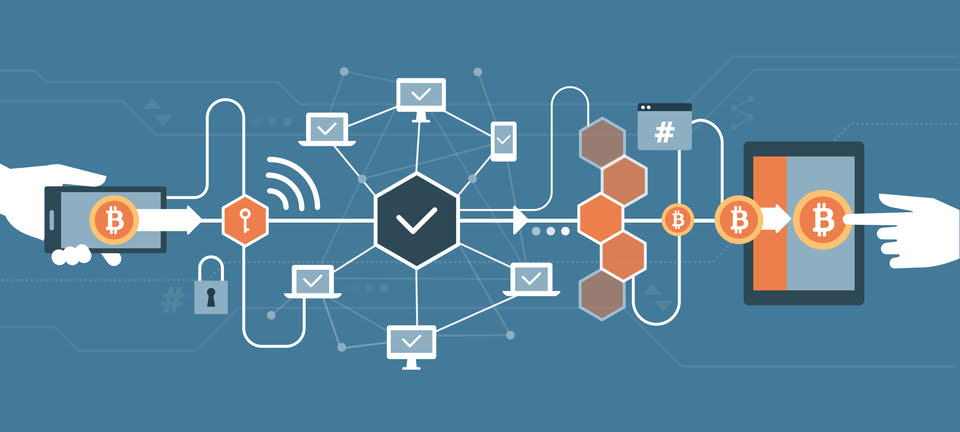
When starting a delivery service business, think about a strategy to keep couriers. They will love flexible working hours, better rates, bonuses, and coverage for travel expenses. To continue the topic of how to build a delivery app technically, we can offer you a high level overview of the on-demand delivery project architecture. The following table explains how to build a delivery app technically.
Checkout Field Editor For Your Website And Mobile App
It’s important to note that while commission fees are lower, GrubHub does not offer logistics, which means that businesses will have to depend on a third-party courier. Access to the Foursquare API starts at $599 for small to medium-sized businesses. New users will need to get an account from the Foursquare website and obtain restaurant app builder the necessary credentials to start sending queries to the API. As part of a special promotion we are offering you app building assistance and expert consultation at ZERO cost. Customers can find different eateries within a particular location. The application will include reviews, ratings, photos, GEO location, and menus.
Just like websites – the best ones are easy to navigate, right? UpMenu system offers you a user-friendly application builder, so you can work on the layout, colors and other visual aspects of your restaurant order apps.
Offer your customers a handy shopping option with our grocery delivery app. Allow restaurant owners to register and create a profile including restaurant address and contact details, a complete menu with prices, and delivery. Grocery Delivery Solutions Offer your customers a handy shopping option with our grocery delivery app.
Instead of a lengthy registration process, users can simply login from a social media platform of their choice. This makes the entire login process quicker and also gives sql server you valuable data that can be used to refine your product. Once you have added the food court feature, click on Save and Continue to finish creating your restaurant app.
To provide a comfortable online ordering and delivery experience, you must research and look into the customer demands to build a perfect app interface. If you are developing an aggregator platform where users can order from nearby restaurants, you have to keep specific ordering ability into consideration. To have users place orders redundantly, the ordering experience that you deliver matters the most. With the restaurant delivery industry’s changing trend, it is possible to win over customers with the latest app designed for enhanced productivity. Get your team together- Choose what part of your business they can access, whether they are an admin, take care of billing, edit content, manage customer service or/and process orders. Our on demand app services can offer you with some of the most affordable development prices in the whole industry. You can find out an estimate cost for your On-demand app solution using our mobile app cost estimator to get a better idea of the costing.
With the changing trend, the main goal of crafting a restaurant app has also changed. Most customers check the restaurant-related information online before purchasing from their brand.



